Integrate the Trust Center
You can embed the Trust Center into your website as a fully integrated component, ideally suited for two main scenarios:
- Authenticated customer account page (post-login)
In this setup, the Trust Center component receives a JWT token to recognize that the user is already authenticated. - Public page (without login)
Here, the Trust Center handles user authentication directly by initiating a one-time passcode login flow.
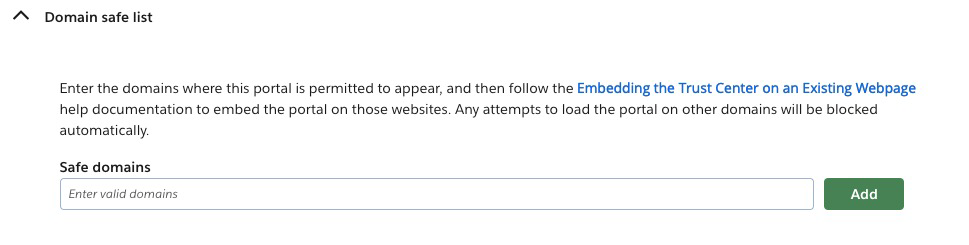
Authorizing permitted domains
To ensure the Trust Center successfully loads on the required websites, you must first specify the domains where the portal will be allowed to load. This list of domains must be entered within the Domain safe list section on the Settings tab of your portal within the OneTrust Platform. This step is required to authorize those domains. Any attempts to load the portal on domains that are not entered within the Domain safe list will be blocked automatically.
For more information, see Configuring Settings for a Trust Center.
Testing the embedded Trust Center
Trust Center can be embedded in any web application, including those built with Vanilla JavaScript, Angular, React, Vue, etc.
To embed the Trust Center into an HTML page, you will need two code snippets:
- A custom
HTMLplaceholder tag. This marks the location where the Trust Center component will be rendered and loaded. - A script to load the required data. This initializes and configures the component with the necessary information.
HTML tag
<trust-center
tenantId="Your tenant UUID"
portalId="Your portal UUID"
blobUrl="https://${privacyportal-domain}"
workerUrl="https://portal-api.onetrust.com"
></trust-center>tenantId: Your user ID.
portalId: The ID of the portal to be loaded.
blobUrl: Environment-specific Azure storage blob URL, such as https://privacyportal.onetrust.com. This URL will vary based on your environment. For more information, see Privacy Portal URLs.
workerUrl: https://portal-api.onetrust.com
Script
<script
src="https://${privacyportal-domain}/portal-trust-center/trust-center/scripts/portal-sdk.js"
type="text/javascript"
></script>Place this script at the bottom of your HTML page (just before the closing </body> tag). Once these two code snippets are added, the portal will load where the placeholder is located.
Passing user identifiers to OneTrust
Prerequisites
- A reliable way to identify a user.
- The ability to create a JSON Web Token (JWT). This will be passed to OneTrust servers to authenticate your request to access a user's consent profile.
For more information, see Jwt.io.
- Upload a Public Key for the generated JWT in your OneTrust tenant.
- Navigate to Settings.
- Under the Consent sub-section, click Public Keys.
- Click the Add Public Key button and then Save.
Creating JWT Auth Tokens
OneTrust does not create the JWT, this needs to be created by your team.
As a security best practice, we recommend generating the JWTs server-side. In this section, we will use the JWT.io as a way to demonstrate the JWT auth token setup.
- Go to JWT.io.
- In the Decoded > PAYLOAD: DATA section, add the unique user identifier as the value for
"sub". - In the Decoded > VERIFY SIGNATURE section, add a value for
your-256-bit-secret.
This value is your Public Key, which you need to add to your OneTrust tenant via Settings > Consent > Public Keys.
- In the Encoded section, copy the value. This will be your Auth Token in the Cookies and Mobile SDK Cross Device Consent configurations.
Website setup
- Identify the user. This can be done using your existing authentication methods.
- Configure the
OneTrustJavaScript variable:id: Unique user identifier.isAnonymous: Set asfalseto create/update user profiles in OneTrust.token: The JWT that you produce with the unique user identifier.
<script>
var OneTrust = {
dataSubjectParams: {
id: "[Insert User ID Here]",
isAnonymous: false,
token : '[Insert JWT Here]'
}
};
</script>Font size inheritance for the embedded Trust Center
To maintain visual consistency between the embedded Trust Center and the parent site, it is recommended to define the font-size at the root level of the parent site. This behavior follows standard CSS inheritance rules and helps ensure a seamless integration experience.
:root {
font-size: ROOT_ELEMENT_FONT_SIZE;
}- If a root-level
font-sizeis set, the embedded Trust Center will inherit this value automatically, ensuring alignment with the parent site's typography. - If no root-level
font-sizeis defined, the Trust Center will default to the browser’s standard font size (typically 16px), which may result in it appearing disproportionately larger than the surrounding content.
Loading the embedded Trust Center
When the page loads, the Trust Center will automatically authenticate using the details passed. Authentication will fail if the user does not have a data subject profile or any DSAR requests assigned to the Trust Center's organization.
Translations for the embedded Trust Center
About language determination
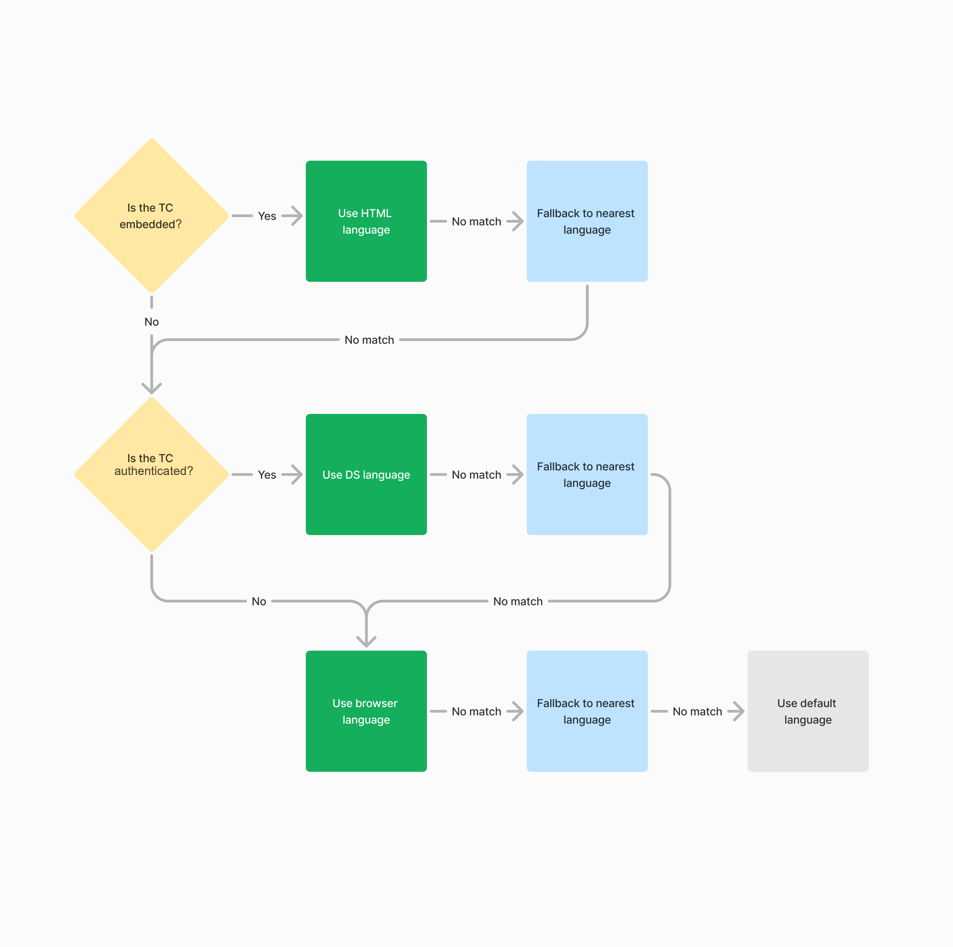
The following scenarios will determine what translation displays when users access the Trust Center.
- If the Trust Center is embedded:
- The translation corresponding to the HTML language displays.
- If a translation matching the HTML language is not enabled, the Trust Center then leverages the fallback language (e.g., if the language
en-usis not enabled, the Trust Center will look foren). - If a translation matching the fallback language is not enabled, the Trust Center checks for authentication.
- If the user is authenticated:
- The data subject's preferred language displays.
- If a translation matching the data subject language is not enabled, the Trust Center then leverages the fallback language.
- If a translation matching the fallback language is not enabled, the browser language displays.
- If the Trust Center is neither embedded nor authenticated:
- The browser language displays.
- If a translation matching the browser language is not enabled, the Trust Center then leverages the fallback language.
- If a translation matching the fallback language is not enabled, the default language displays.
Available Trust Center languages
| Language code | Language | Is regional variant |
|---|---|---|
| af | Afrikaans | ❌ |
| am | Amharic | ❌ |
| ar | Arabic | ❌ |
| ar-ae | Arabic (United Arab Emirates) | ✅ |
| ar-bh | Arabic (Bahrain) | ✅ |
| ar-eg | Arabic (Egypt) | ✅ |
| ar-jo | Arabic (Jordan) | ✅ |
| ar-kw | Arabic (Kuwait) | ✅ |
| ar-lb | Arabic (Lebanon) | ✅ |
| ar-om | Arabic (Oman) | ✅ |
| ar-qa | Arabic (Qatar) | ✅ |
| ar-sa | Arabic (Saudi Arabia) | ✅ |
| ar-tn | Arabic (Tunisia) | ✅ |
| az | Azerbaijani | ❌ |
| az-az | Azerbaijani (Azerbaijan) | ✅ |
| be | Belarusian | ❌ |
| be-by | Belarusian (Belarus) | ✅ |
| bg | Bulgarian | ❌ |
| bg-bg | Bulgarian (Bulgaria) | ✅ |
| bn | Bengali | ❌ |
| bs | Bosnian | ❌ |
| bs-ba | Bosnian (Bosnia and Herzegovina) | ✅ |
| ca | Catalan | ❌ |
| co | Corsican | ❌ |
| cs | Czech | ❌ |
| da | Danish | ❌ |
| da-dk | Danish (Denmark) | ✅ |
| de | German | ❌ |
| de-at | German (Austria) | ✅ |
| de-be | German (Belgium) | ✅ |
| de-ch | German (Switzerland) | ✅ |
| de-de | German (Germany) | ✅ |
| de-li | German (Liechtenstein) | ✅ |
| de-lu | German (Luxembourg) | ✅ |
| el | Greek | ❌ |
| el-cy | Greek (Cyprus) | ✅ |
| el-gr | Greek (Greece) | ✅ |
| en | English | ❌ |
| en-au | English (Australia) | ✅ |
| en-bw | English (Botswana) | ✅ |
| en-ca | English (Canada) | ✅ |
| en-gb | English (Great Britain) | ✅ |
| en-ie | English (Ireland) | ✅ |
| en-in | English (India) | ✅ |
| en-nz | English (New Zealand) | ✅ |
| en-sg | English (Singapore) | ✅ |
| en-us | English (U.S.) | ❌ |
| en-za | English (South Africa) | ✅ |
| et | Estonian | ❌ |
| et-ee | Estonian (Estonia) | ✅ |
| eu | Basque | ❌ |
| fi | Finnish | ❌ |
| fi-fi | Finnish (Finland) | ✅ |
| fil | Filipino | ❌ |
| fr | French | ❌ |
| fr-be | French (Belgium) | ✅ |
| fr-ca | French (Canada) | ✅ |
| fr-ch | French (Switzerland) | ✅ |
| fr-dz | French (Algeria) | ✅ |
| fr-fr | French (France) | ✅ |
| fr-lu | French (Luxembourg) | ✅ |
| fr-ma | French (Morocco) | ✅ |
| fr-tn | French (Tunisia) | ✅ |
| fy-nl | Frisian (Netherlands) | ✅ |
| gl | Galician | ❌ |
| hr | Croatian | ❌ |
| hr-hr | Croatian (Croatia) | ✅ |
| hy | Armenian | ❌ |
| hy-am | Armenian (Armenia) | ✅ |
| in-as | Assamese | ❌ |
| in-brx | Bodo | ❌ |
| in-dgo | Dogri | ❌ |
| ka | Georgian | ❌ |
| ka-ge | Georgian (Georgia) | ✅ |
| kl | Greenlandic | ❌ |
| km | Central Khmer | ❌ |
| my | Burmese | ❌ |
| my-mm | Burmese (Myanmar) | ✅ |
| nl | Dutch | ❌ |
| nl-be | Dutch (Belgium) | ✅ |
| nl-nl | Dutch (Netherlands) | ✅ |
| sq | Albanian | ❌ |
| sq-al | Albanian (Albania) | ✅ |
| zh-hans | Chinese (Simplified) | ❌ |
| zh-hant | Chinese (Traditional) | ❌ |